Scenario
You have installed an ODX Server on an Azure VM. The ODX Service is running OK.
You have a number of on-premises machines with TimeXtender Desktop installed. You would like to connect those to the ODX Server on Azure VM.
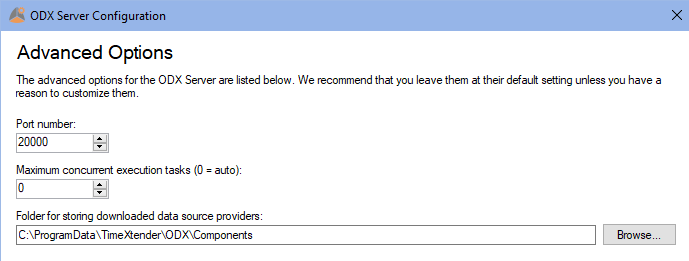
1. Find the ODX port
Lookup the port number in ODX Server Configuration:
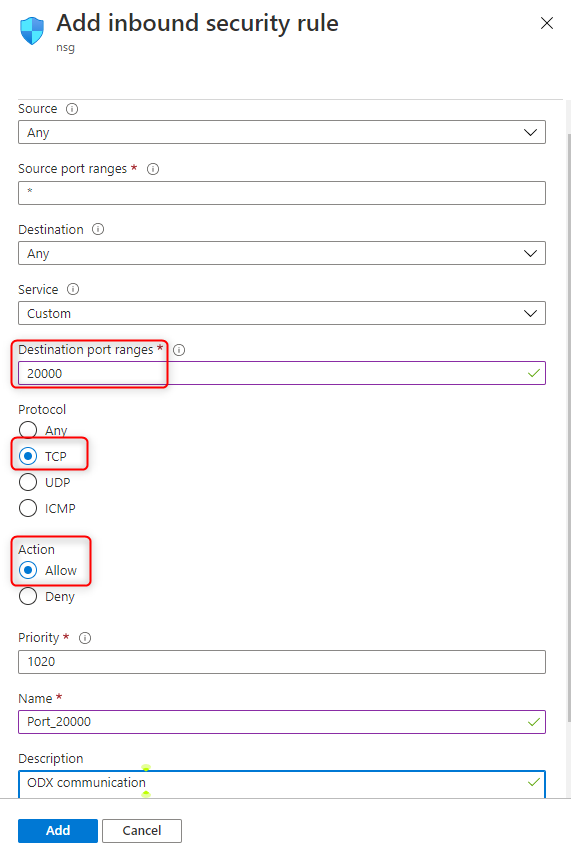
2. Configure the ODX port in Azure VM Network security group inbound rule
In Azure portal, for the resource group associated with your VM, go to
Network security group -> add an inbound security rule
3. Configure the ODX port in Azure VM Windows Defender Firewall
Login (RDP) to Azure VM,
run "Windows Defender Firewall with Advanced Security"
Add an inbound rule for TCP port used in ODX setup:
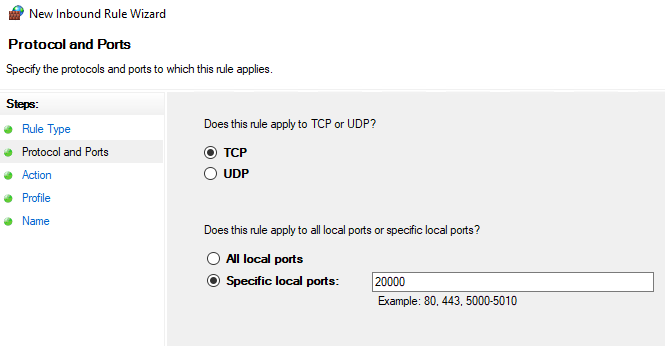
Note: mark the appropriate profile (private or public) as configured for your VM in Azure portal.
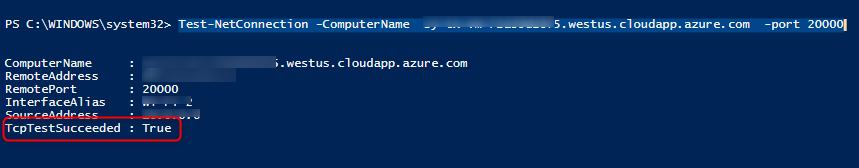
4. Test the port in PowerShell
Note: Ensure the ODX Service is running
Open a PowerShell window to test the following command
Test-NetConnection -ComputerName <fully qualified DNS name of ODX server VM> -port 20000
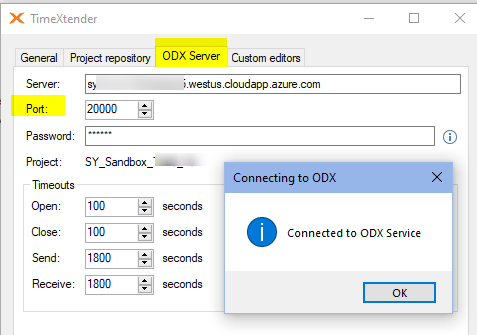
5. Connect your TimeXtender Desktop to the ODX Server
Run TimeXtender Desktop -> Tools -> Options ->ODX Server
Specify the fully qualified DNS name of ODX server, for example:
<vm-name>.westus.cloudapp.azure.com
6. Troubleshooting Common Errors
TCP error code 10060: A connection attempt failed
Could not connect to the ODX Server.
---------------------------
Could not connect to net.tcp://<vm-name>westus.cloudapp.azure.com:20000/OperationalDataExchange. The connection attempt lasted for a time span of 00:00:21.0382698. TCP error code 10060: A connection attempt failed because the connected party did not properly respond after a period of time, or established connection failed because connected host has failed to respond <vm-IP-address>:20000.
Please check that the TimeXtender ODX Service is running on the target machine and that there is no firewall blocking the communication.
---------------------------
This is a generic error, with several potential causes. For example:
- You have not configured the ODX port in Azure VM Network security group inbound rules
- You have not configured the ODX port in Azure VM Windows Defender Firewall inbound rules
- The appropriate profile (private or public) is not checked in Windows Defender Firewall inbound rule. It should match the appropriate profile (private or public) configured for your VM in Azure portal.
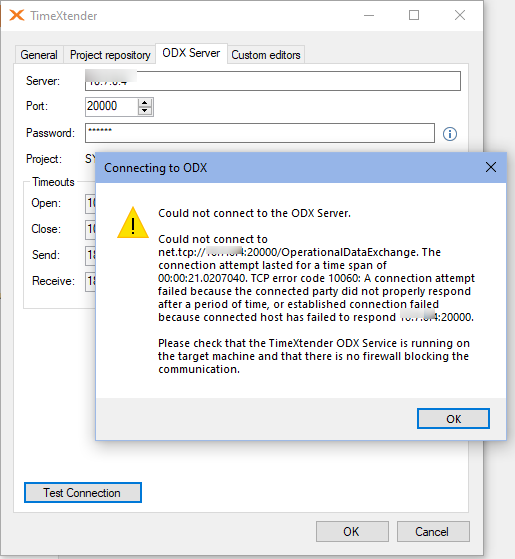
- You have specified the VM's private IP address. You need to specify its public IP address
No DNS entries exist for host:
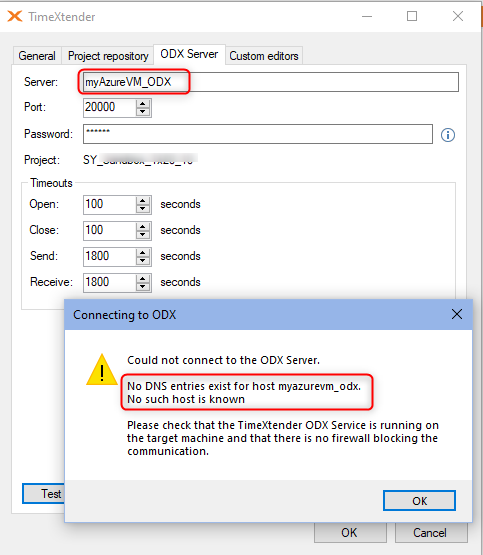
Cause: You are trying to specify the first prefix name
Resolution: Use a fully qualified DNS name, for example
<vm-name>.westus.cloudapp.azure.com
The communication object, System.ServiceModel.Channels.ServiceChannel, cannot be used for communication because it is in the Faulted state.
Cause: You are trying to specify a gateway IP address
Resolution: specify the VM's direct public IP address
0 Comments