TimeXtender can connect and extract data from a Dynamics 365 Sales instance using the CData Dynamics 365 Sales ADO.NET Provider. You may find more information on using this provider from the CData Provider Help Guide here.
This guide is broken down into multiple steps:
Create an App Registration in Azure Active Directory
For Dynamics 365 to authenticate a connection from an external application, you must first create an App Registration in Azure Active Directory. You can learn more about this process from Microsoft here, however, more direct steps are provided below.
Create the App Registration
- In the Azure Portal, navigate to Azure Active Directory
- Select App Registrations in the menu bar on the left & Select New Registration.
- Enter a name and select Accounts in any organizational directory (Multitenant).
- Enter a redirect URI, This can be something generic like (http://localhost:33333) or you may use your Organizational URL for your Dynamics instance (https://<company>.crm4.dynamics.com/).
- Select Register when you are done.
- Note down the Application ID which will be used later.
Create the App Secret
- After creating the App Registration, select Certificates & secrets.
- Select New Client Secret.
- Provide a description of the secret, and a duration. When done, select Add. (This key is encrypted after save, so it needs to be documented somewhere safe.)
- Note down the Client Secret Value which will be used later.
Add the API Permission
- Under the App Registration menu Select API Permissions.
- Select Add a permission
- Under Microsoft APIs, select Dynamics CRM
- Select Delegated permissions, then select user_impersonation, & click Add permissions
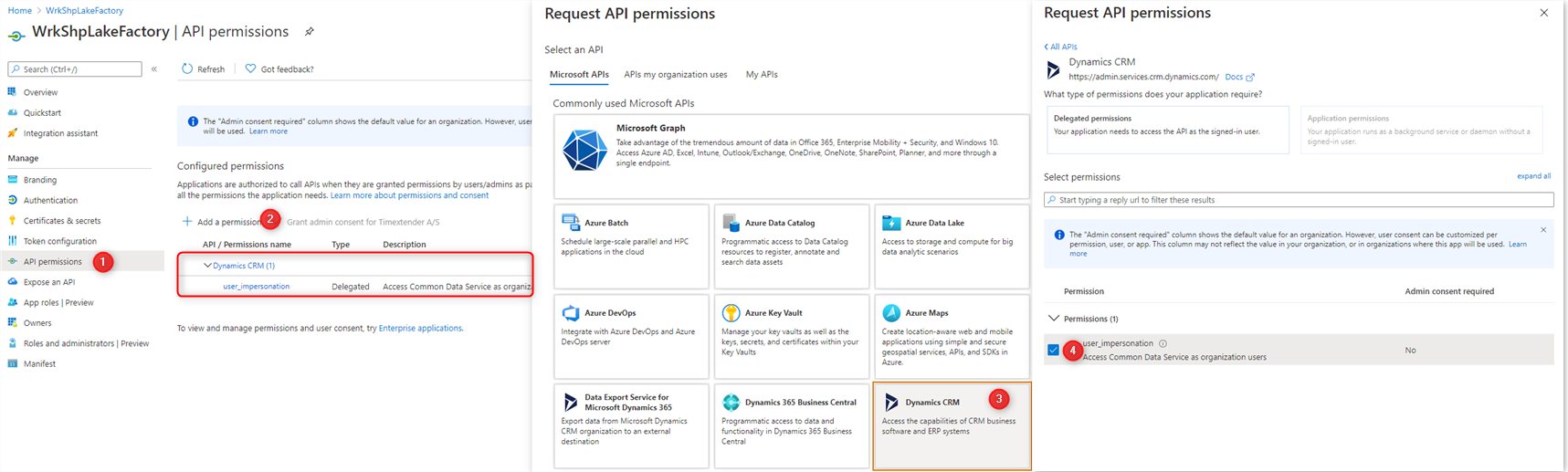
The API permission should look like it appears in the red box above.
Add the Data Source in TimeXtender
This data source can be found by navigating to the Dynamics 365 Sales CData provider in the list of availabel CData providers either in the ODX or the Business Unit.
Once you have added the data source configure the connection values as described below
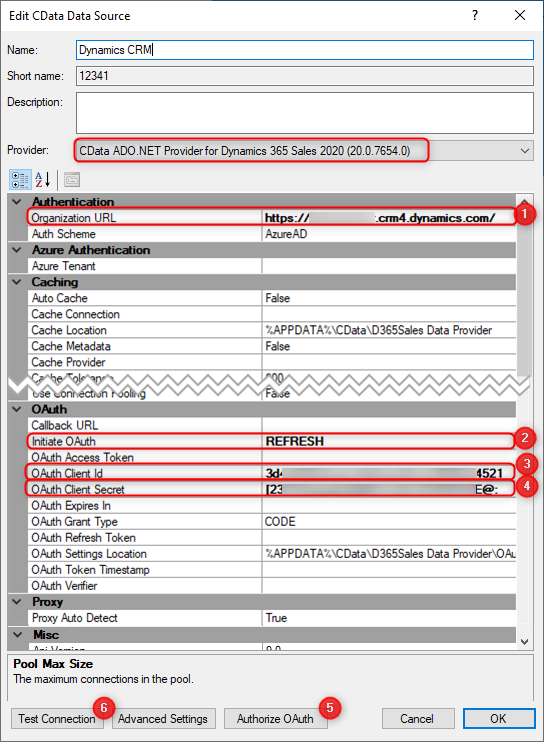
Configure the Data Source Connection
- Enter your Organization URL for you Dynamics Instance. This should appear similar to https://<company>.crm4.dynamics.com/.
- Scroll down to the OAuth section of connection string options and set Initiate OAuth to REFRESH
- Set the OAuth Client Id to the Application ID of the App Registration created earlier.
- Set the OAuth Client Secret to the Client Secret of the App Registration created earlier.
- Click the Authorize OAuth button. This should launch a web browser and authorize your connection to Dynamics.
-
Add a specific OAuth Settings Location path to the file instead of the default. It works fine for testing, but when using scheduled executions in a BU the file will not exist for the service to use.
- Click the Test Connection button to ensure you have connected successfully.
Use the Client Credentials method
You also have the options of using Client credentials to gain access.
Client Credentials
Client credentials refers to a flow in OAuth where there is no direct user authentication taking place. Instead, credentials are created for just the app itself. All tasks taken by the app are done without a default user context. This makes the authentication flow a bit different from standard.
Client OAuth Flow
All permissions related to the client oauth flow require admin consent. This means the app embedded with the CData ADO.NET Provider for Dynamics 365 Sales cannot be used in the client oauth flow. You must create your own OAuth app in order to use client credentials. See Creating a Custom OAuth App for more details.
In your App Registration in portal.azure.com, navigate to API Permissions and select the Microsoft Graph permissions. There are two distinct sets of permissions - Delegated and Application permissions. The permissions used during client credential authentication are under Application Permissions. Select the applicable permissions you require for your integration.
In addition to setting the standard OAuth client id and secret, to use client credentials you must also set the following connection properties:
- OAuthGrantType: Set this to CLIENT.
- AzureTenant: Set this to the tenant you wish to connect to.
When you authenticate using client credentials, there is no Web flow. Authentication with client credentials will take place automatically like any other connection, except there will be no window opened prompting the user. Because there is no user context, there is no need for a browser popup. Connections will take place and be handled internally.
1 Comments